When it comes to data breaches and securing the company digital systems against hackers, most small businesses typically adopt the “ostrich head in the sand” approach. Owners always believe that cyber criminals are more likely to target the corporate giants and have no interest in the smaller fry.
The reality is far from this perception. If you’re an entrepreneur who regularly collects and uses sensitive information from customers, employees, and business partners, then your business is most definitely at risk.
The Ponemon Institute 2016 Cost of Data Breach Study warns that the per capita cost of data breaches has been steadily rising over the years. Further, cases of data breaches in the United States alone are far higher than what the world is experiencing. Take a look at this graph and you will understand the impact of the phenomenon on global businesses.
Tips to Protect Your Business and Secure It’s Data
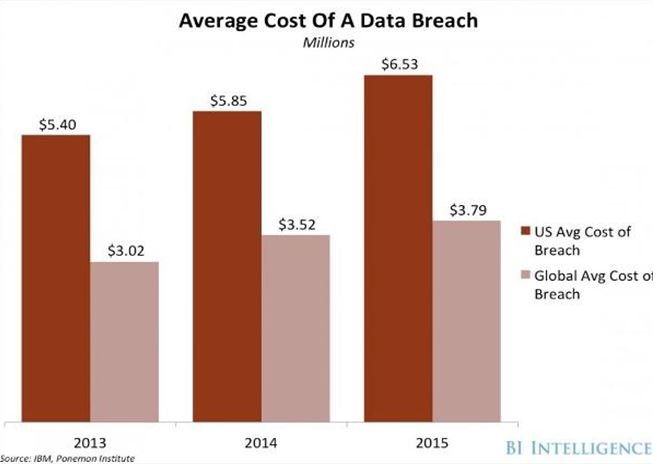
Source – Business Insider
In the face of the threat of data breaches possibly wiping out your entire business, know that by taking precautions and staying up-to-date with the latest developments of the cyber world, you can keep your business protected. Read ahead about a few smart tools you can use.
Train Your Employees How to Deal with Personal Information
The Identity Theft Resource Center’s 2014 Data Breach Category Summary reveals that two main reasons for leaks in sensitive data have emerged. The first being the loss of hardware containing the information such as cell phones, laptops, and other devices. And, secondly, employees handling data using unsecured networks and via devices not authorized by their company.
Your best bet is to conduct detailed workshops and training programs for your employees educating them on the importance of secure data management. You may have a BYOD policy where workers use their own devices or you may have a system where you assign refurbished laptops, cellphones, and other equipment to your workers. Instruct them to use the gadgets responsibly and inform the company right away in case of loss of the hardware or any suspected leak of data.
Have detailed protocols in place for onsite and offsite employees especially if you outsource company operations regularly. Outlining an exit strategy for retiring and fired employees can also help secure sensitive data.

Bring in the Experts to Assess Your Digital Systems
Companies are constantly evolving entities and as you grow and expand operations, your new business models may not be secure enough. Even healthcare organizations put themselves at risk when their medical records aren’t stored and managed efficiently. Hire the services of expert evaluation agencies that can come in from time to time to assess your digital systems.
They will help you by identifying the weak links and levels of risk of data breaches. Use their recommendations to deploy the necessary security applications and programs to protect your company.
Install Encrypting Programs
Make sure all devices used for managing sensitive information have encrypting programs installed in them. However, relying solely on this form of data security is not enough. That’s because, experienced cyber criminals with advanced skills have been known to crack the encrypted data also.
Get other security measures such as two-step authentication, restricting multiple login attempts, identifying questions, firewall protection, complicated passwords, and other applications advised by the IT evaluation team.
Keep Your Systems Updates with the Latest Protective Technology
As long as you’re using Microsoft operating systems, you only need to install all the updates you receive information about. However, if you’re using any other systems like Mac, Linux, or UNIX, you need other patching applications. Institute a company policy to remain updated with the latest patches that can keep your systems protected.

Restrict the Amount of Data You Collect and Save
The best way to deter potential hackers is non-availability of valuable information. Here’s how:
- Harvest data only if it is absolutely essential.
- Restrict the number of devices it is saved on.
- Separate the servers through which the data passes.
- Hire expert data destruction services that can shred documents, hard drives, and SSDs according to the mandatory procedures laid down by the federal government.
- Disallow the transfer of information into removable devices such as pen drives and burnable CDs that can be stolen.
- If you must dispatch data, use authorized courier services and tamper proof packaging.
- Choose secure cloud storage for saving the data you need to provide products and services to your customers.
- Track information as it passes through the different departments so it is possible to identify any source of leaks.
Install Intrusion Detection Applications
Your IT security team can help you install intrusion detection applications that identify hacking attempts, issue warnings, and prevent them. You’ll also need monitoring programs that can track the movement of visitors through your company website.
Be aware that cyber criminals can break into your digital systems by browsing through the website. Make sure you have programs that can block visitors from accessing sensitive areas and have them monitored regularly for effectiveness.
Clearly Define and Institute Failsafe Measures
Train your employees to identify signs that indicate a data breach has occurred. Institute a detailed data loss protection protocol that will kick into place the instant a hacker enters your systems. Having such failsafe measures in place will ensure your workers know how to act and company operations continue undisturbed. Research has proved that such measures can lower the average loss from a breach up to $21 per record.
By using these 7 strategies, you can minimize the possibility of data breaches and significant losses resulting from them.
In addition to securing your company digital systems, you must also hold vendors and partnering businesses accountable. Clearly inform them that you expect adherence to federal regulations when dealing with your company. Every step you take can ensure security and the lasting success of the business you’ve created.
Join 25,000+ smart readers—don’t miss out!








1 Comment
Protecting your business from data breaches is essential in today’s digital world. Start by implementing strong password policies and enabling multi-factor authentication to secure accounts. Regularly update software and systems to patch vulnerabilities that hackers could exploit. Train employees on cybersecurity best practices, such as identifying phishing emails and avoiding suspicious links. Encrypt sensitive data, both at rest and in transit, to prevent unauthorized access. Limit access to critical information only to those who need it and monitor user activities to detect unusual behavior. Use reliable firewalls, antivirus programs, and intrusion detection systems to safeguard your network. Regular data backups are also crucial, ensuring that you can recover quickly if an attack occurs. Finally, develop and test an incident response plan so your team knows how to act swiftly during a breach. Proactive strategies like these help protect your business’s reputation, finances, and customer trust.