Small and midsized businesses are often targets for cyber-attacks not just because they have valuable data, but also because they may not have the same level of security as larger businesses. That’s why it’s important for SMBs to understand penetration testing and what it can do for them.
In this blog post, we’ll discuss why SMBs should pentest their systems, what the key drivers of pentesting are, and how they can benefit from it.

What is Penetration Testing?
Penetration testing, also known as “pentesting” or “pen test,” is a security exercise where your computer system is subject to a simulated attack with the goal of finding out exploitable vulnerabilities. This type of test is important because it can help you to find and fix security weaknesses before they are exploited by real attackers.
What is the process of Penetration Testing?
We usually divide the pentest process into three phases.
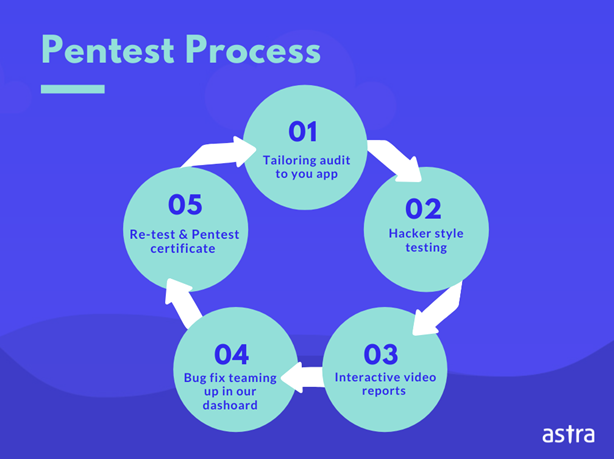
The Pre-attack Phase: In this phase, you will define the objectives of the penetration test, identify which systems will be tested, and determine the rules of engagement.
This phase also includes the reconnaissance activity where the pentesters learn as much as possible about the target through passive and active information gathering tactics.
The Attack Phase: In this phase, the target is scanned for vulnerabilities. The vulnerabilities discovered are then exploited to gain insights into their severity, potential damage, cost of exploitation, chances of privilege escalation, etc.
The Post-attack phase: Once the scan and exploitation are done, it is usually time for risk analysis and report building. The insights gathered from the attack phase are examined to create an image of the security posture of a company, and the same is conveyed through a detailed, systematic report that includes steps and suggestions for fixing the discovered vulnerabilities.
What are the key drivers of penetration testing?
The key drivers of penetration testing can be divided into three categories.
- Compliance: Many compliance frameworks, such as PCI DSS, SOX, and HIPAA, require penetration testing to be performed on a regular basis.
- Risk management: In order to properly manage the risks associated with their systems and data, businesses need to know what those risks are. Penetration testing can help you spot the risks so that they can be analyzed, managed, and controlled.
- Vendor assessment: When you offer your services to another organization, they might ask you if you have pen-tested your systems. This is one of the key drivers of penetration testing for SMBs
How should SMBs approach penetration testing?
There is no one-size-fits-all answer to this question, as the approach depends on the specific needs and goals of each organization. However, we recommend that SMBs start by doing a self-assessment of their systems and data to identify potential risks.
Once potential risks have been identified, penetration testing can be used to validate those risks and determine the best way to mitigate them. You can have a difficult start, but with the right pentest partner, you start realizing the benefits pretty fast. Here’s what an SMB needs.
Hacker-style penetration testing
Trained security experts perform a controlled attack on your system using the same tactics as a hacker would, to detect exploitable vulnerabilities. The security experts would then be able to create a report on the loopholes in your security and give you a near accurate idea of how much damage each of those vulnerabilities could have resulted in.
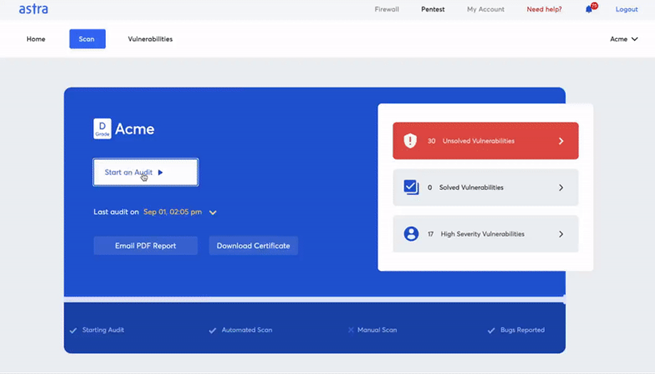
Seek a pentest provider that offers both automated and manual pentest
Automated pentest is a fast and inexpensive way of detecting common vulnerabilities in your system, but if your business deals with a lot of sensitive information and manages payment gateways, it is wise to have manual penetration testing done at least twice a year. Only a manual pentest detects business logic errors and payment manipulation hacks.
Continuous automated scanning through CI/CD integration

It helps if you can integrate an automated scanner with your CI/CD pipeline. It means the scanner will automatically detect vulnerabilities whenever you try to push some new code into your application. Look for a tool that integrates easily with platforms like GitLab, GitHub, Jenkins, Bitbucket, Jira, and Slack.
A tool that makes vulnerability management easy

You should be able to monitor vulnerabilities, follow your compliance status, assign vulnerabilities to your team, and collaborate with security experts from the pentest vendor, all from one place. Ideally, an interactive dashboard that brings it all together.
How does a business benefit from penetration testing?
Penetration testing can help businesses to improve their overall security posture by identifying and fixing vulnerabilities before they are exploited. In addition, penetration testing can help you stay compliant with various security regulations.
Finally, penetration testing can also be used as a way to assess the security of vendors who offer services to your organization.
- You get a deeper understanding of the cyber safety of your business.
- You gain an understanding of the potential damage caused by the present vulnerabilities.
- The pentest report helps your developers fix those vulnerabilities
- That in turn helps you achieve compliance.
- Build trust among customers
- Enter new markets.
How should an SMB choose a pentest partner?
The first is to make sure that the partner has experience working with businesses of your size and in your industry.
The second is to ensure that the partner has a good understanding of your specific needs and goals for the penetration test. Finally, you should also ask for references from past clients to get a sense of the partner’s quality of work.
Conclusion
Penetration testing is an important activity for businesses of all sizes, but it is often overlooked or misunderstood by small and midsized businesses. We hope that this post has helped to provide some clarity on what penetration testing is and why it is important.